m0n0wall with certificate from Enterprise CA
In order to use m0n0wall (or any other) any other firewall than m0n0wall as DirectAccess Network Location Service (NLS) server, we need to create a SSL certificate from trusted CA. You may want to consider this if you have clustered firewall and Directaccess (DA). NLS is essential for DA clients if they are on LAN. If your router of firewall dies, DA will propably be one of your last worries.
There is no tools in m0n0wall to create private key and CSR. This is how to do it with OpenSSL for Windows and Windows Server CA tools.
Generate private key and CSR with OpenSSL
This command will create private key and Certificate Signing Request. Fill the information as needed.
openssl.exe req -new -newkey rsa:2048 -nodes -keyout fw.laituri.local.key -out fw.laituri.local.csr
You have to convert private key to PEM form:
openssl.exe rsa -in fw.laituri.local.key -outform PEM -out fw.laituri.local.key.pem
Windows server CA
Copy .csr to your CA server. You cannot create SSL certificate in Enterprise CA using graphical tools. You need to define template used in creation process and GUI does not support that.
Logged on as user with privileges to enroll certificates, type:
certreq -submit -attrib "CertificateTemplate:WebServer" c:\Data\fw.laituri.local\fw.laituri.local.csr
Active Directory Enrollment Policy
{8E5C0F2E-0F5F-4019-9F20-89082913FF2C}
ldap:
RequestId: 8
RequestId: "8"
Certificate retrieved(Issued) Issued
Application will prompt for CA to be used and where to save .cer file.
m0n0wall setup
Backup your configuration (and firewall virtual machine).
- In general setup: select webGUI protocol to HTTPS
- In Advanced setup, under webGUI SSL certificate/key, copy content of fw.laituri.local.cer to Certificate-field and content of fw.laituri.local.key.pem to Key-field.
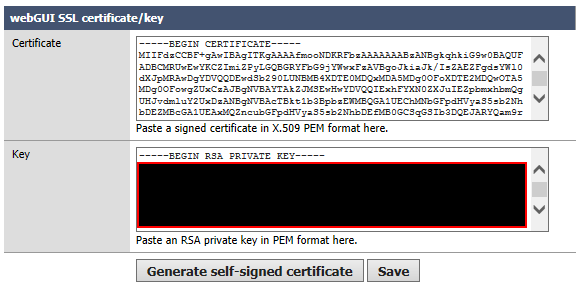
Save and reboot. After firewall has restarted, verify it's connectivity with HTTPS protocol. If you loose connectivity, you can restore virtal machine from backup and figure it out without hurry.
NLS configuration
Verify requirements to move NLS role to firewall.
- Your firewall has static A-record in DNS
- Workstations trust to issued SSL sertificate (navigate to management web page with DNS name)
- CA CRL can be accessed
- Firewall DNS name is excluded in NRPT table (DA settings step 3)
- You have scheduled check and renewal process for firewall certificate
After this you can move network location server to your firewall (DA settings step 3).
Update
I never got this to work with m0n0wall. I know from experience that this is working idea. I am quite sure, that this is becouse m0n0wall welcomes client with HTTP 401 "Unauthorized" instead of HTTP 200 "OK". If firewall logon page would be normal HTTP page, this would work.